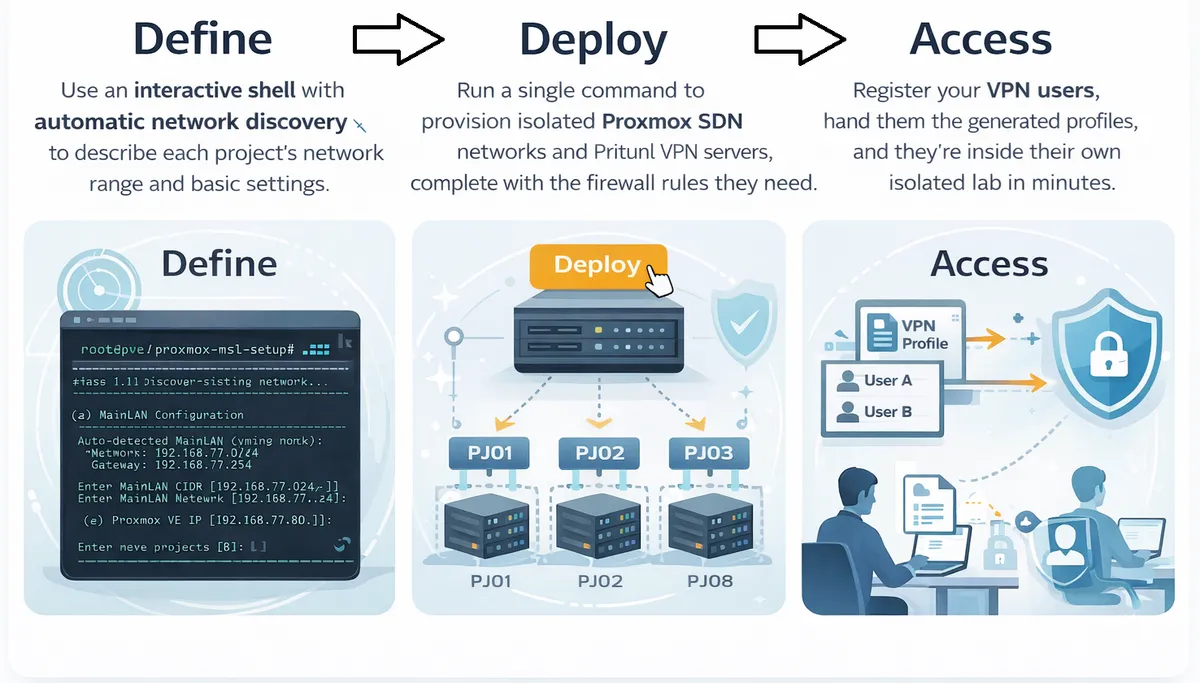
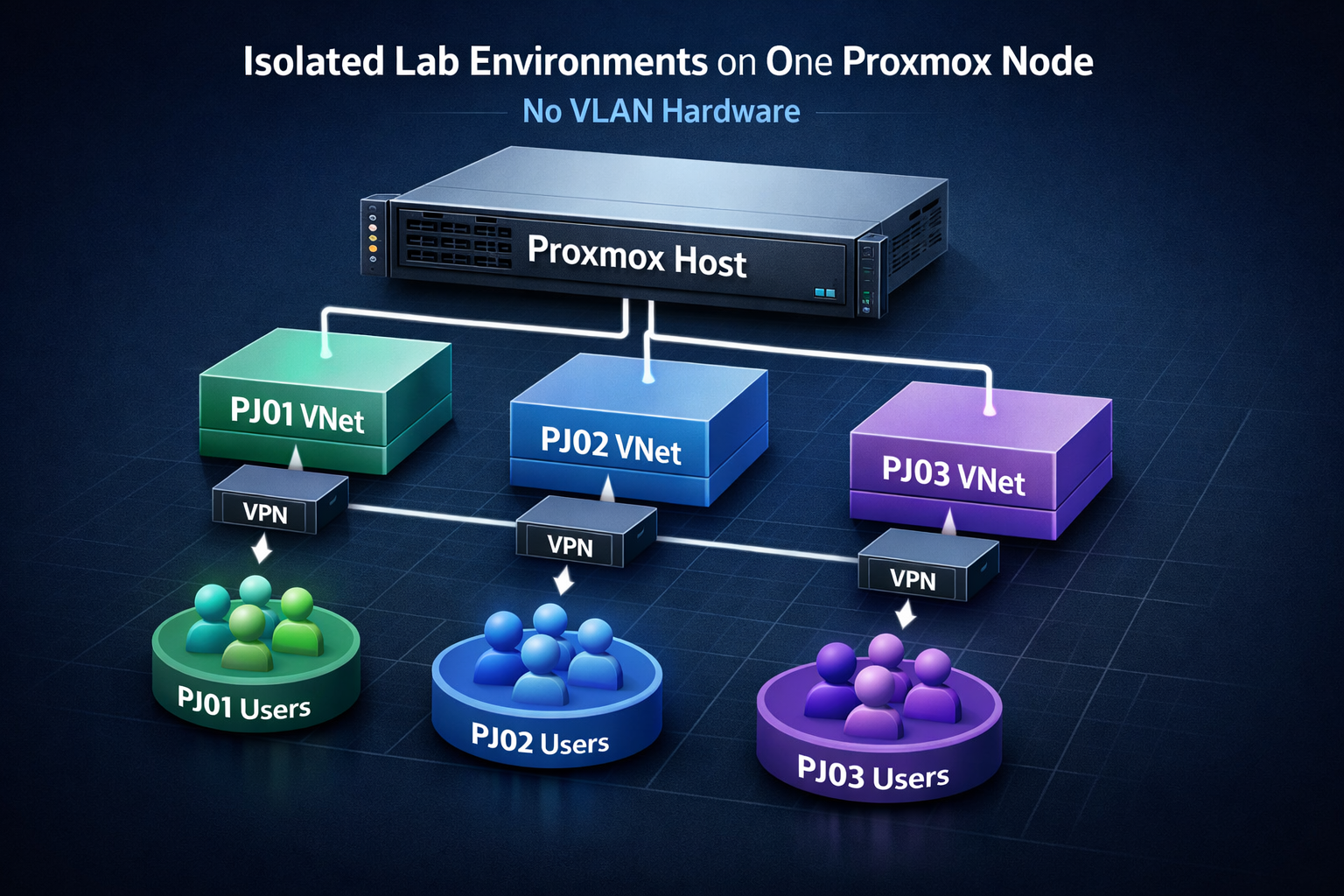
MSL Setup can be used for various purposes such as all software development companies, OT, game server fault localization, etc.:
- Want to quickly prepare a high-performance distributed development environment on-premises
- Need an environment where demos, PoC environments, and verifications can be prepared easily, securely, and cost-efficiently
- Want to isolate each network to localize faults from various threats
- Client projects must be strictly separated from each other
- Want to conduct vulnerability testing in a closed network
- Want to quickly launch an MSP lab
- Want to quickly launch many virtual appliance integration test environments with L2-level isolated networks
- Want to reduce the risk to the production environment by building development and staging environments in-house
- Want to efficiently manage VMs without worrying about costs such as snapshots and backup generations
- Want to efficiently manage customer training environments on a single server
This is why this project exists: to provide a way to quickly deploy multi-tenant environments — without turning every environment into a security incident waiting to happen.